Bettercap Network Sniffing
Bettercap, this All-in-one MITM Toolkit, provides opportunity to do packet sniffing. It can intercept all the traffic in the local machine, the incoming/outgoing traffic. It can be used to do password capturing while filtering.
Let’s start sniffing:
Warning: make sure you have bettercap installed in your system, if not check our previous article explaining how to install it.
First let us launch bettercap:
Bettercap
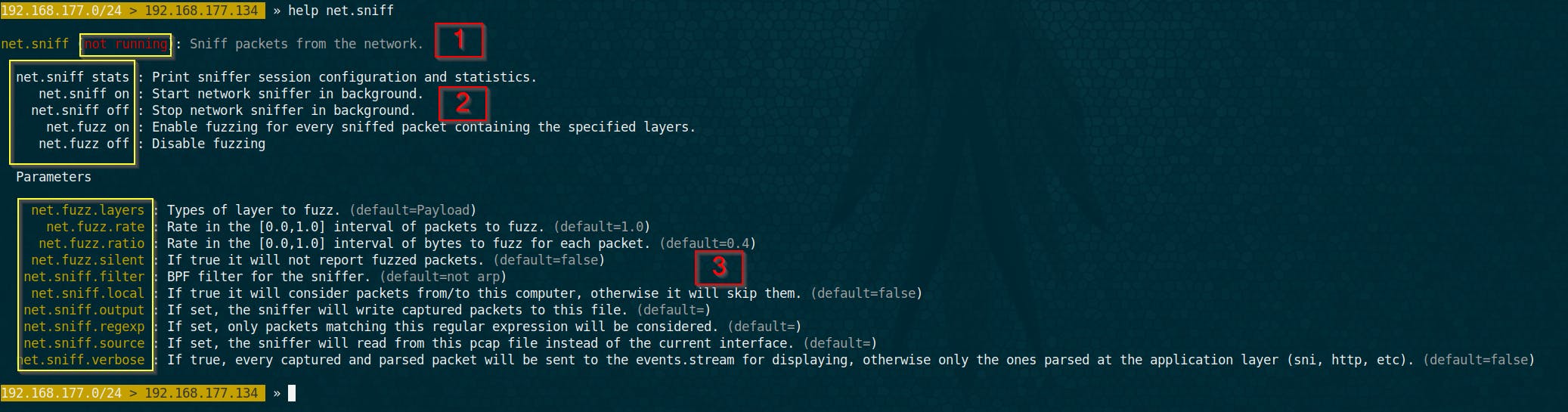
The module responsable for the sniffing is called net.sniff. To see how we can use it, we can check the help section.
help
We can see that We have three important section in the help section
- Section 1: indicates the state of the module whether running/not running
- Section 2: indicates the different ways we can launch the net sniffing module
- Section 3: are the different options to be configured based on what you want to perform. These options have default settings unless you modify them.
For example if we want to capture every packet transiting over our machine from ARP to the protocols of application layer (http,ftp,…) we should set the options net.sniff.verbose to true as follows :
set net.sniff.verbose true
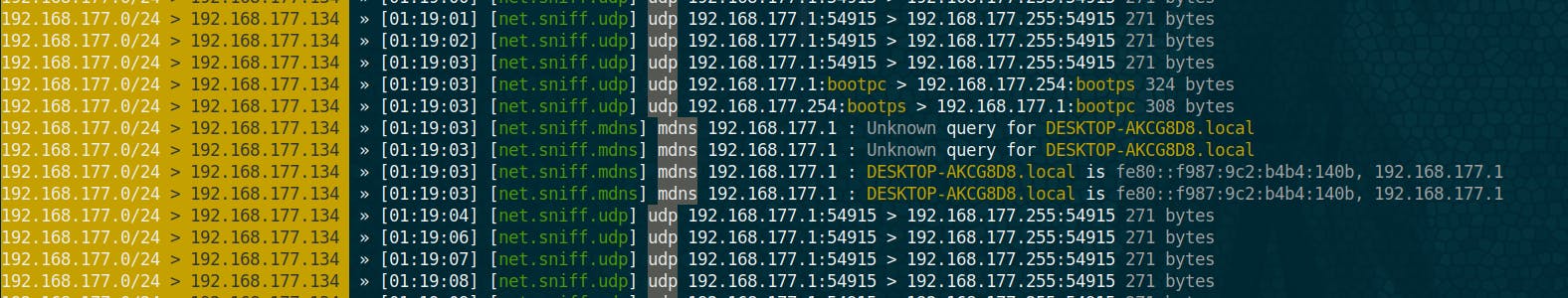
now to launch the sniffing module: net.sniff on
you may get something on your screen as follows:
The verbose mode may sometimes be too informative, we may only want to capture packets that we generated on our local machine . To do that , let’s disable the verbose mode first:
net.sniff off
set net.sniff.verbose false
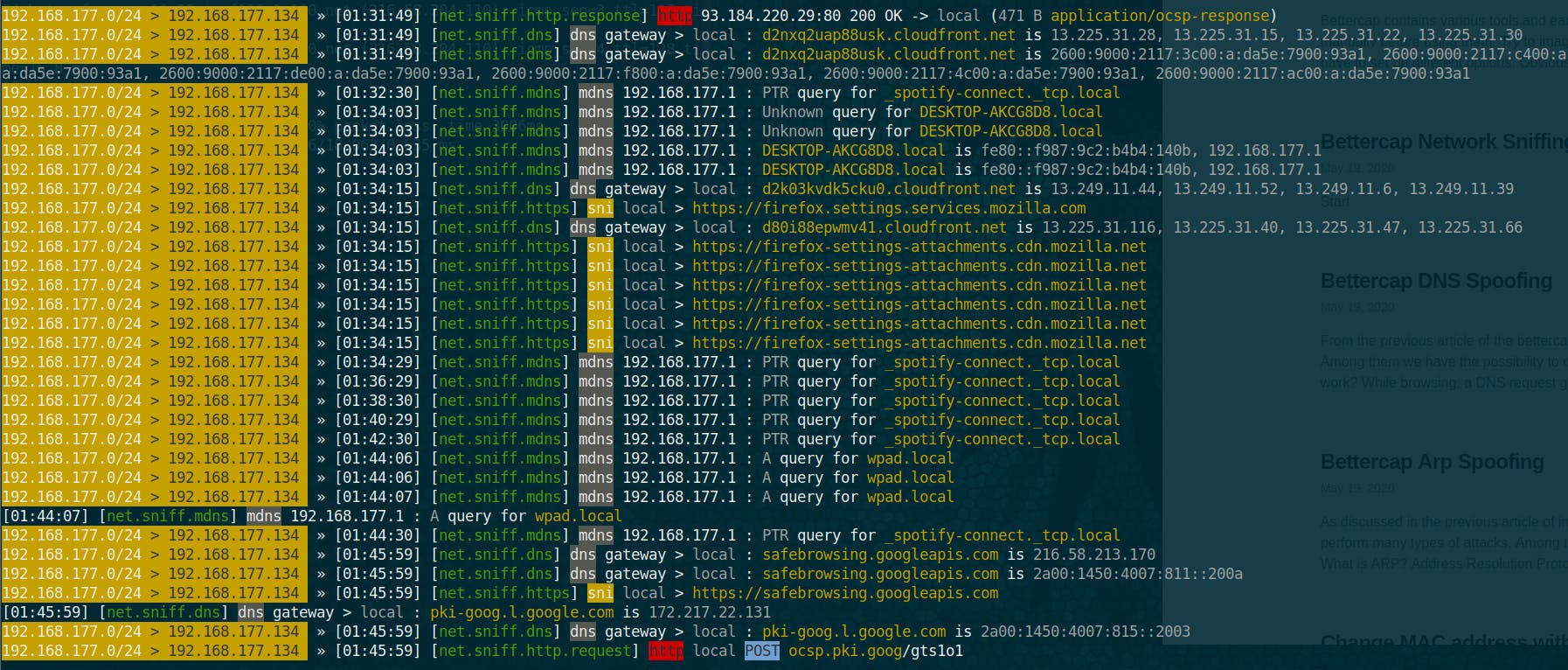
Now to sniff, parse and print packets that are generated by our actions, we have to define the option net.sniff.local to true. To do that:
set net.sniff.local true
To launch the packet sniffing: net.sniff on
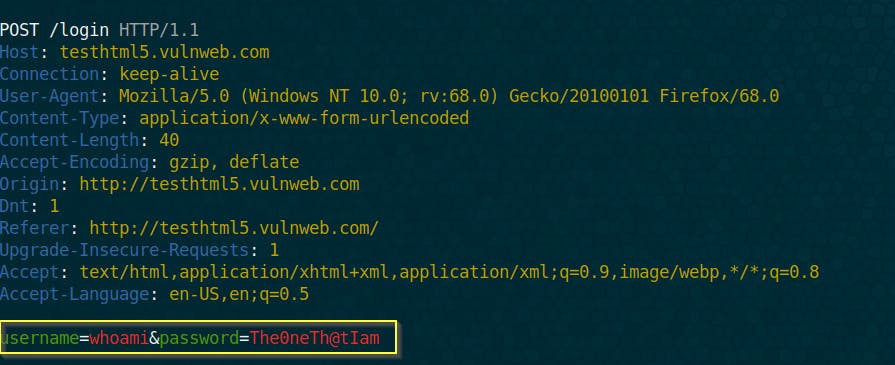
You could also set bettercap in such a way that it captures only logins and passwords. You want it to ignore the others request and only display to you a login and password that it captured. To so so, we use the option net.sniff.regexp. As we can see , we need to define a matching pattern, to the information we want to capture. Since we want to capture passwords , we define it as follows:
set net.sniff.regexp ‘.*password=.+’
run the sniffing: net.sniff on
After capturing some credentials you may wonder how to save it in a file so that you can use it later. Bettercap give you the opportunity to do so with the option net.sniff.output
For a previous example, if we want to save the credentials in a file "‘credentials.pcap’’, we have to set the option responsible of it to true:
set net.sniff.output credentials.pcap
run sniffing: net.sniff on
After it captured a password it displays it on the screen and create a file called credentials.pcap as specified and save the login and password in it
As we can see on the shell 2 , the file has been created and contains the login and password captured.
This is where our paths diverge. Of course we havent see all the features of net.sniiff of bettercap, with what we’ve seen you can do some necessary stuffs relating to sniffing. If you want more information, check the manual of the module by typing help net.sniff and dont forget to get a look at the official documentation of bettercap.
Thanks for reading, if you struggle make sure to comment bellow and I will be glad to help.
Feel free to check the tutorials I have posted about bettercap tools. Have fun.